2022年 春秋杯网络安全联赛 冬季赛 WriteUp
大概是第一次在i春秋摸到 Top1(这题都能吃,我真是小馋猫)
Misc [AK]
reindeer game
pyinstaller解包,直接调pyc里生成flag的函数: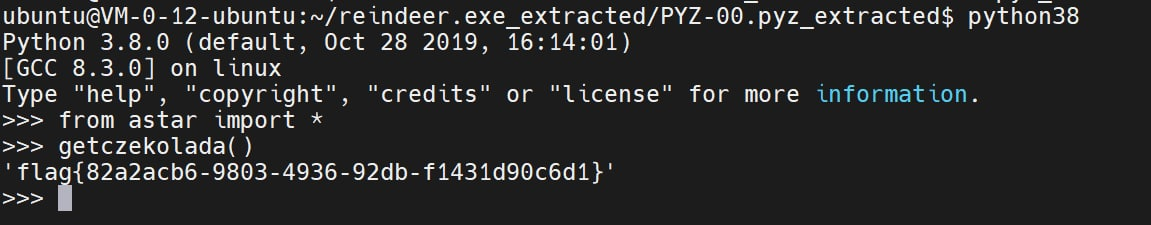
楠之勇者传
轻松拿到魔法棒,然后按提示去 /proc/self/mem 找地方写sc
自己开了个环境看一下nobody跑的python36居然是没随机化地址的,然后本地偏移通了远程不过(版本是一样的)
于是远程先按0x1000加偏移,卡死了就逐byte加,然后就成功执行到了shellcode
1 | from pwn import * |
问卷
问卷
nan’s analysis
图片..没什么用
压缩包,有密码,但其实就是删了root密码的shell,带回车..也没什么用
唯一有用的是FTP的密码,是AES的key
iv猜了好久,最后用UTF8的16个0搞出来看起来很对的字符,但长度不对
然后用0504重复4次做IV得到了正确的root密码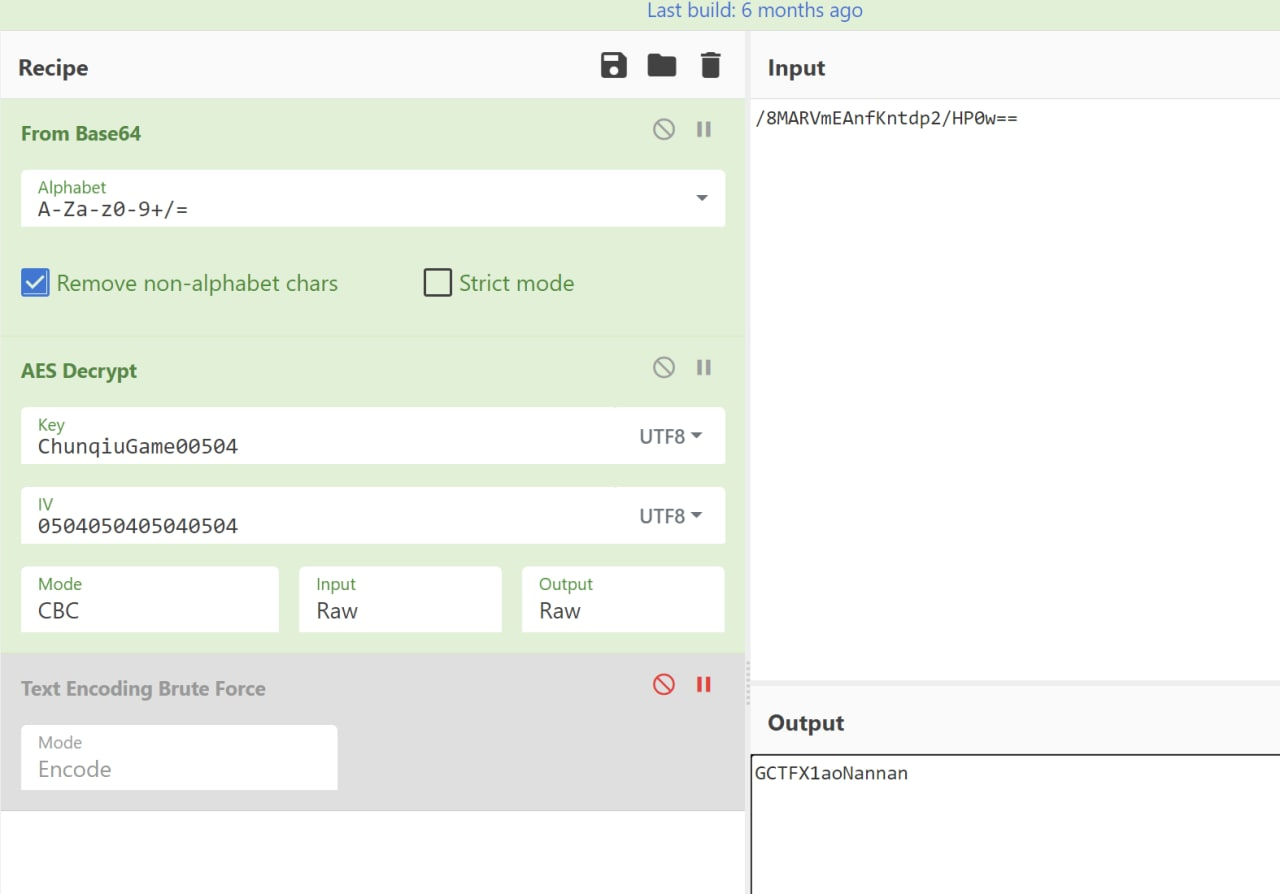
shell的位置ls -la对比几下就找到了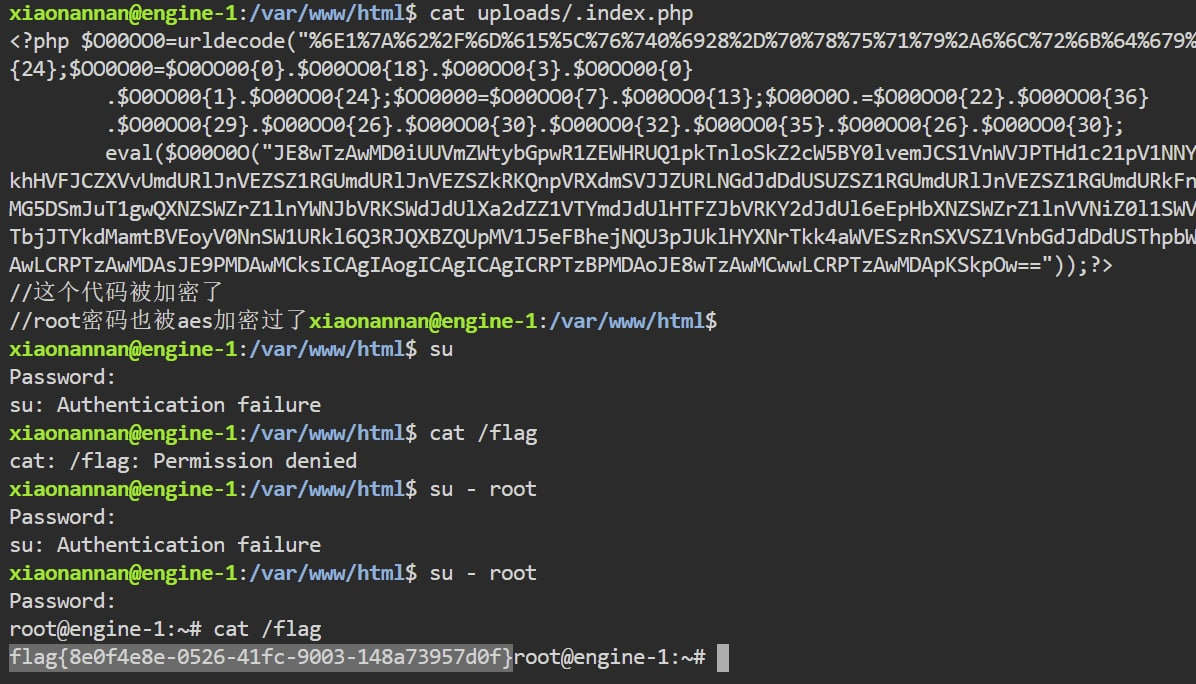
PWN
work_pwn
有一秒钟的时间等待线程,在一秒之内改全局变量就行了
1 | from pwn import * |
online_judge
没有执行权限,文件系统只读
二分可以偷东西出来(AC, WA)
一开始不知道/flag是目录,痛失一血
打了一堆东西出来,甚至把环境变量都偷了出来
1 | import os |
RE [AK]
godeep
自动化逆向现在大家都会了(好多解)
这里命名是IDA7.7自动改的,7.7比7.5对go的支持好了很多'godeep_tree.VSWEwsr'是right输出的函数'godeep_tree.ApSzXJOjiFA'是main里开始的函数
按if的内容01一下,然后把01串反过来就是flag
1 | name = 'godeep_tree.VSWEwsr' |
easy_python [三血]
正向还原字节码
1 | r = [204, 141, 44, 236, 111, 140, 140, 76, 44, 172, 7, 7, 39, 165, 70, 7, 39, 166, 165, 134, 134, 140, 204, 165, 7, 39, |
baby_transform [三血]
鉴定为傅里叶变换,逆变换是: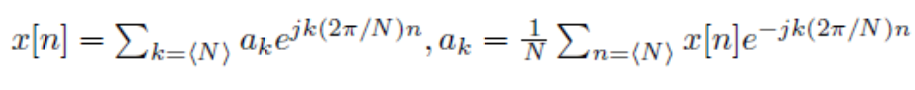
欧拉欧拉欧拉 $e^{(jx)}=cosx+jsinx$ 结束
1 |
|
Web
ezphp
我不知道php8有什么魔法特性,但我知道 $3 * 37 = 111$
然后传个 ?num=3*37 就..过了
一开始想到0x然后0被墙了,然后想逻辑拼接,===后接个|2什么的,然后就想到位运算,但是位运算长度不太够,然后去factordb找乘法找到3*37,回来时候已经3解了,大家秒的都好快
2022年 春秋杯网络安全联赛 冬季赛 WriteUp