Setting up AFL++ and fuzzing mcrypt
我的计算机安全课件设计:AFL++环境配置以及上手一个简单的fuzz任务。
My computer security course materials: AFL++ environment setup and getting started with a simple fuzzing task.
这部分材料是我为计算机安全课程中fuzz部分准备的,因为我很菜又需要找一个(网上没有答案的)真实的crash,所以用的CVE是很老的QAQ。
This section of material was prepared for the fuzzing portion of my computer security course. To ensure the course quality, I need to find a real crash that didn’t already have answers online, so I ended up using a rather old CVE.
我为计安课准备的其他材料还有:
Other materials I prepared for the course (CS 315, Computer Security at SUSTech) include:
- Buffer Overflow
- Lecture 课件: Detailed explained how buffer overflow works and discussed some classical protections.
- Lab 实验指导: Seed lab in Ubuntu24 plus: (avoid white-space characters in shellcode) + (vulnbility repair) + (question about ASLR and PIE) + (bonus for ASLR bypassing)
- Lab attachments 实验材料
- Return-to-libc (In detail!)
- Lecture 课件: Demostarte what happens when we launch a ROP attack and discuss about CFI protections.
- Lab 实验指导: Pwn a ret2libc challenge and try protections like Canary, ASLR, NX, SafeStack, PAC…
- Lab attachments 实验材料
- Fuzzing & Symbolic Execution
- Lecture 课件: Talk about the idea of fuzzing and symbolic execution.
- Lab 实验指导: Definitely N0t reversing CEC-IDE or other things!
- Lab attachments 实验材料
Fuzzing task instruction
mcrypt is a small tool but supports many encryption algorithms. It is widely use in many web applications like php. In this lab, we will use AFL++ to find a real crash in mcrypt-2.6.5 (CVE-2012-4409).
CVE-2012-4409 happens when mcrypt decrypts a file.
If you find any new crash not on record, please report it to the maintainer.
Setup AFL++ environment
Note below steps will install shared libs in your Virtual Machine, be careful if you are using your own machine and don’t want to install shared libs.

1 Compile AFL++:
1 | sudo apt update |
2 Fuzz binary in previous lab
First create a directory for input and output files:
1 | sudo su |
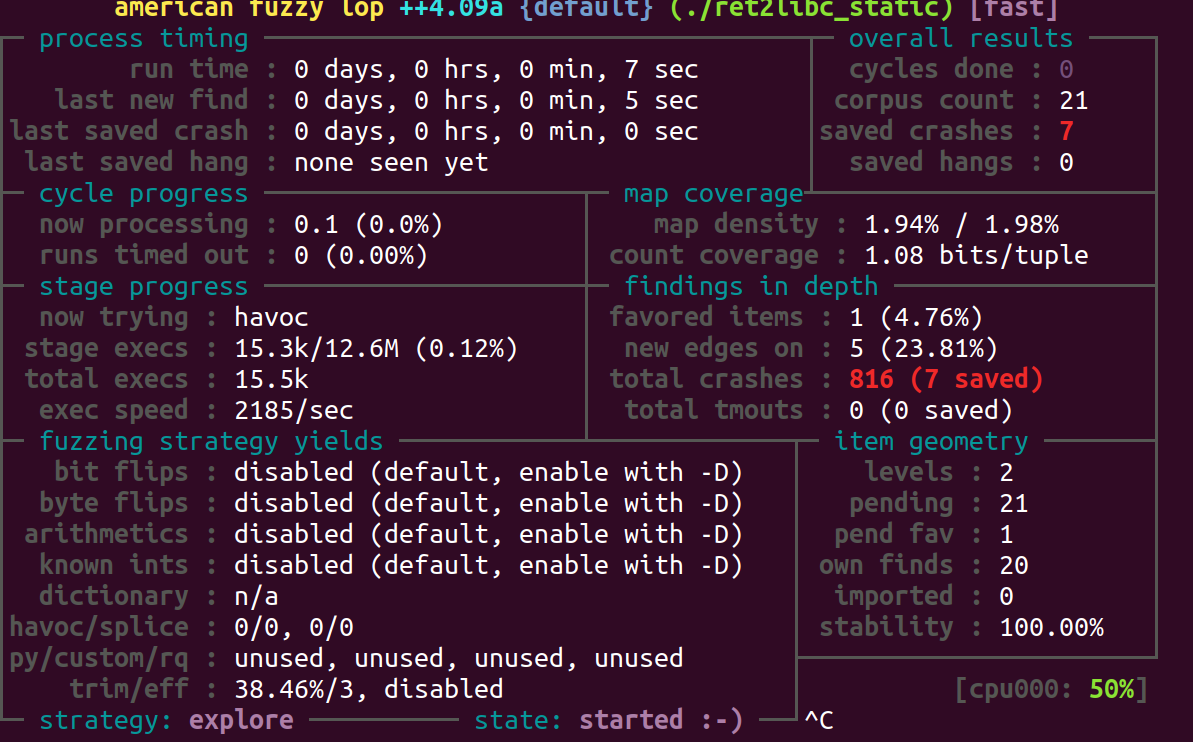
AFL may find crash quickly.
The crash can be found in outputs/default/crashes/
3 compile mcrypt
1 | tar -zxvf mhash-0.9.9.9.tar.gz |
Now you should have mcrypt in src/ directory (in mcrypt-2.6.5/src/).
Firstly, open a new terminal and run:while true; do rm outputs/default/.cur_input.dc;done;
Then use afl-fuzz -i inputs/ -o outputs/ -- ./mcrypt arg1 arg2 (change agr1
and arg2 to real argument!!) to fuzz mcrypt program, if some arguments represent file, you can use @@ to represent the file.
If you need to stop and re-start the fuzzing, use the same command line options and switch the input directory with a dash (-):afl-fuzz -i - -o outputs/ -- ./mcrypt arg1 arg2
This time, AFL may not find crash quickly, we can create a more vaild input for mcrypt to help AFL reach more code and find crash.
1 | echo "random input" > raw_text |
Setting up AFL++ and fuzzing mcrypt